Email Scams
Email scams are on the rise in 2023. And each year, they become trickier and more realistic. Learn how to identify phishing emails, scams , and stay safe. You’ll find the latest phishing email here updated as I find them.
Envision you saw this in your inbox. From the get go, this email looks genuine, yet entirely it’s not. Tricksters who send messages like this one are trusting you won’t see it’s a phony.
Here are signs that this email is a trick, despite the fact that it seems as though it comes from an organization you know — and even purposes the organization’s logo in the header:
The email has a nonexclusive hello.
The email says your record is waiting a direct result of a charging issue.
The email welcomes you to tap on a connection to refresh your installment subtleties.
While genuine organizations could speak with you by email, real organizations won’t email or text with a connection to refresh your installment data. Phishing messages can frequently have genuine ramifications for individuals who give tricksters their data, including fraud. Also, they could hurt the standing of the organizations they’re ridiculing.

How To Recognize Phishing
In order to steal your passwords, account numbers, or Social Security numbers, scammers use email or text messages. The most common is the phishing scam email. The information they get could give them access to your email, bank account, or other accounts. It is also possible that they will sell your information to another scammer. These kinds of phishing attacks are launched by scammers every day – and they’re often successful.
Envision you saw this in your inbox.
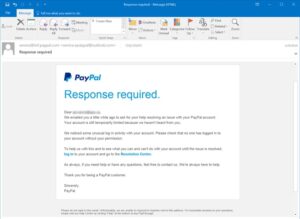
From the get-go, this email looks genuine, yet it’s not. Tricksters who send messages like this one are trusting you won’t see it’s a phony.
Here are signs that this email is a trick, despite the fact that it seems as though it comes from an organization you know—and even purposes the organization’s logo in the header:
The email has a nonexclusive hello.
The email says your record is waiting as a direct result of a charging issue.
The email welcomes you to tap on a connection to refresh your installment subtleties.
While genuine organizations could speak with you by email, real organizations won’t email or text with a connection to refresh your installment data. Phishing messages can frequently have genuine ramifications for individuals who give tricksters their data, including fraud. Also, they could hurt the standing of the organizations they’re ridiculing.
How to stop phishing emails
Phishing emails might be kept out of your inbox by your email spam filters. But scammers are always trying to outsmart spam filters, so extra layers of protection can help. Here are four ways to protect yourself from phishing attacks.
The most effective method to Safeguard Yourself From Phishing Assaults
Your email spam channels could keep numerous phishing messages out of your inbox. Yet, con artists are continuously attempting to outmaneuver spam channels, so additional layers of security can help. The following are four methods for shielding yourself from phishing assaults.
Four Methods for safeguarding Yourself From Phishing
1. Safeguard your PC by utilizing security programming. Set the product to refresh naturally so it will manage any new security dangers.
2. Safeguard your phone by setting programming to naturally refresh. These updates could give you basic insurance against security dangers.
3. Safeguard your records by utilizing multifaceted validation. A few records offer additional security by requiring at least two qualifications to sign in to your record. This is called multifaceted validation. The additional accreditations you want to sign in to your record fall into three classes:
something you know — like a password, a PIN, or the solution to a security question.
something you have — like a one-time confirmation password you get by text, email, or from an authenticator application; or a security key
something you are — like a sweep of your finger impression, your retina, or your face
Multifaceted verification makes it harder for tricksters to sign in to your records in the event that they really do get your username and secret word.
4. Safeguard your information by sponsorship it up. Back up the information on your PC to an outside hard drive or in the cloud. Back up the information on your telephone, as well.
Report internet scams and phishing
How To Report Phishing
Report Scam Email
What to do with suspicious emails
Report internet scams and phishing
If you got a phishing email or text message, report it. The information you give helps fight scammers.
- If you got a phishing email, forward it to the Anti-Phishing Working Group at reportphishing@apwg.org.
- If you got a phishing text message, forward it to SPAM (7726).
- Report the phishing attempt to the FTC at ReportFraud.ftc.gov.
Report phishing emails and text messages if you receive them. The information you give helps fight scammers.
- If you got a phishing email, forward it to the Anti-Phishing Working Group at reportphishing@apwg.org.
- If you got a phishing text message, forward it to SPAM (7726).
Report the phishing attempt to the FTC at ReportFraud.ftc.gov.
What To Do in the event that You Suspect a Phishing Assault
On the off chance that you receive an email or an instant message that requests that you click on a connection or open a connection, answer this inquiry:
Do I have a record with the organization or know the individual who reached me?
In the event that the response is “No,” it very well may be a phishing trick. Return and survey the exhortation in How to perceive phishing and search for indications of a phishing trick. On the off chance that you see them, report the message and erase it.
In the event that the response is “Yes,” contact the organization utilizing a telephone number or site you know is genuine — not the data in the email. Connections and connections could introduce hurtful malware.
What To Do on the off chance that You Answered a Phishing Email
On the off chance that you think a trickster has your data, similar to your Government backed retirement, Visa, or ledger number, go to IdentityTheft.gov. There you’ll see the particular moves toward take in light of the data that you lost.
Assuming that you assume you tapped on a connection or opened a connection that downloaded hurtful programming, update your PC’s security programming. Then, at that point, run a sweep and eliminate anything it recognizes as an issue.
Related:
How to Stop Spam in Your Inbox:Taming the Email Monsters in 2023